Tesla, cracked ......
In the last two days, David Colombo, a 19-year-old German boy working on cybersecurity research, recently made a big discovery.

While conducting a security review for a French company, he noticed that a software program in the company's network had leaked all the data about the Tesla driven by the company's CTO, including the car's driving record and precise location at the time.
But that wasn't all. As the investigation progressed, Colombo realized that he could push commands to the Tesla that used the program. This allowed him to hijack some of the car's functions, including opening and closing doors/windows, turning up music, playing videos, enabling keyless driving and disabling security features. However, he was unable to control the car's steering, braking and other operations.
Colombo's discovery has sparked a lively discussion on Twitter. With the ubiquity of IoT devices, cybersecurity is on everyone's mind.
In a tweet posted Jan. 11, Colombo said he had been able to push commands to at least one car in each country. Subsequent analysis suggests that number could expand to hundreds of vehicles.
It's worth noting that the flaws don't exist in Tesla's cars or on Tesla's network, but in an open-source software that collects and analyzes data from its own cars.
After discovering these issues, Colombo contacted Tesla's security team. He provided the team with screenshots and other documents that explained his findings in detail and identified the manufacturer of the affected third-party software, but did not release the details to the press.
The team then began its investigation. A spokesperson for the National Highway Traffic Safety Administration also said it has been in contact with Tesla about the matter and that the agency's cybersecurity technical team will assist in evaluating and reviewing the information.
Since Colombo did not provide detailed information about the software, Twitter users are making their own guesses. For example, many people are linking Tesla's thousands of expired authentication tokens to the incident.
However, Tesla explained that the vulnerability reported by Colombo involved a different platform. Since that platform uses V2 Tesla tokens, which have all expired, no TezLab users are at risk because of the vulnerability described in David's post.
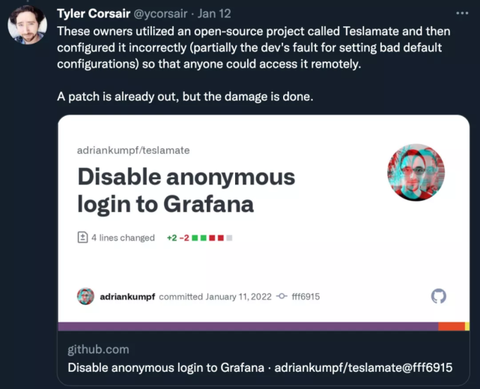
Tyler Corsair, founder of Teslascope, also clarified on Twitter, "Those users mentioned by Colombo used an open source project called Teslamate and then misconfigured it (in part because the developers set the wrong default configuration) so that anyone could access it remotely." After receiving the report, they have rolled out a patch.
Started programming at age 10, started company at 15
Specializing in cybersecurity, Colombo claims to have "written his first code at the age of 10" and that his company's goal is to "help protect every business from the evolving threat actors in cyberspace.
When his mother developed breast cancer when he was 13 and died the following year, he chose to further immerse himself in programming as a distraction.
After growing tired of the pace of school, he and his father successfully applied for a waiver when he was 15, allowing him to attend school only two days a week and spend the rest of his time expanding his cybersecurity skills and building a consulting firm called Colombo Technology.
"I had to study Latin and literary analysis, and then I wondered, why? I could focus on the security side of things to protect my company," he said, adding that he thought school "was a waste of time.
Colombo said he is involved in several "vulnerability bounty" programs, where some companies offer bounties to independent security researchers for finding weaknesses in their products and seek advice from companies that help them assess security.
How vulnerable are connected cars?
Of course, this isn't the first time cybersecurity personnel have disclosed potentially serious security vulnerabilities involving Internet-connected cars. in 2015, two security researchers disclosed an attack in which a reporter for Wired magazine remotely took control of a Jeep Cherokee and shut down its engine while driving the car at 70 miles per hour on a U.S. highway. The automaker recalled 1.4 million cars and trucks because of a defective Internet-connected infotainment system, the first automotive recall to be triggered by cybersecurity concerns.
Since then, researchers have begun disclosing many other hacking risks they have discovered, which increasingly come from within the complex electronics of vehicles.
Shortly after the Jeep hack came to light, another group of researchers disclosed software flaws in the Tesla Model S that could have allowed hackers to shut down the engine of a moving car. After the researchers coordinated with Tesla, the latter released a software fix.
In 2020, the autopilot of the Tesla Model X was repeatedly hacked. In one case, researchers at Ben-Gurion University in Israel tricked cars into accidentally braking or steering in the wrong direction by flashing 'phantom' images on roads, walls or signs.
A few months later, Lennert Wouters, a researcher at the University of Leuven in Belgium, "stole" a Tesla Model X in 90 seconds.
Last fall at the 2021 World Congress on New Energy Vehicles, Musk promised that he would work with regulators to ensure that the personal data of electric car owners is protected from hacking threats.
"With the rapid development of self-driving technology, the security of vehicle data is more of a public concern than ever before," Musk said. By 2025, an estimated 470 million vehicles will be connected to computerized databases, making them ripe targets for cybercriminals.
Colombo said he reached out to three Tesla owners in Germany, the United States and Ireland before disclosing his findings. He showed a screenshot of a private conversation on Twitter in which one of the affected owners allowed him to remotely honk the car's horn to confirm the existence of the breach.
After failing to find contact information for most of the other Tesla owners whose data was compromised, he decided to publish his findings.
"I wanted to give owners a heads up, and that was the original intent," he said. "Because if I didn't, maybe someone with malicious intent would have found those system vulnerabilities and done something with bad intent. Imagine that someone could take control of your Tesla, open the doors and take it for a drive.






























